Best Practices in Zecurion DLP Deployment

1. Make the complex simple. Start small, when introducing a new (or first) DLP to your organization. Pilot test in key areas, configure the solution upon your needs, and arrange the most required reports first. It’s always better to take everything from your solution than to pay for something extra that will go unused. For an easy start, Zecurion DLP has more than 20 preset powerful reports to quickly drill down to a specific incident in a few clicks.
2. Decide, where your network needs active protection. Comprehensive data loss prevention needs to monitor and analyze activities with minimal impact on the productivity of the ‘ecosystem’. Zecurion Traffic Control can function as either an active filter (in real-time), or it can analyze mirrored traffic. To make a decision, use the phased option – start with a mirrored setup to test policies and fine-tune them for maximum efficiency and then set up active filtering mode.
3. Create deployment option of your own. Every corporate environment is a unique mix of network segments, endpoint types, operating systems, different platforms, and applications. Zecurion provides a diverse range of deployment options to ensure your data is monitored and protected no matter what your network infrastructure looks like. Below are the most common deployment options. Be sure to consult a Zecurion Sales Representative to choose the best one for your IT infrastructure.
With blocking: Email
Plugin for Microsoft Exchange
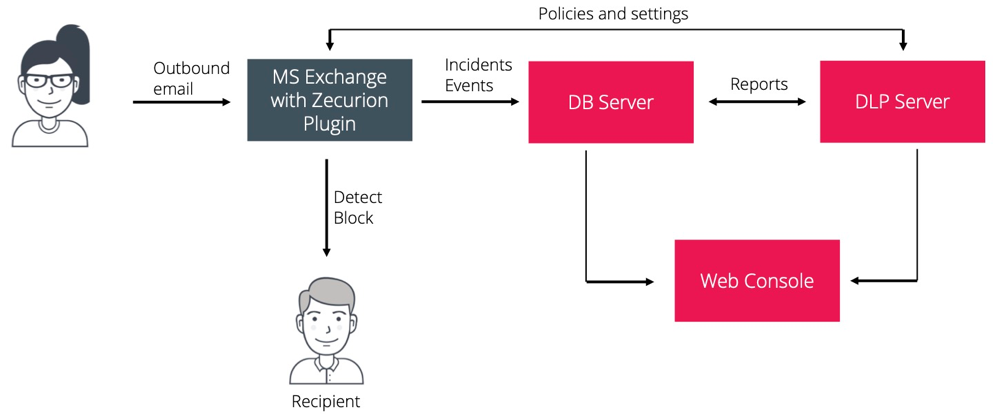
Benefits: Simplicity of settings and further maintenance, reliable email blocking.
Note: Installation in MS Exchange transport, requiring a safety margin for hardware resources on MS Exchange servers.
Configuring the routing of mail traffic in a blocking mode (Zecurion Traffic Control acts as an SMTP Mail Relay server)
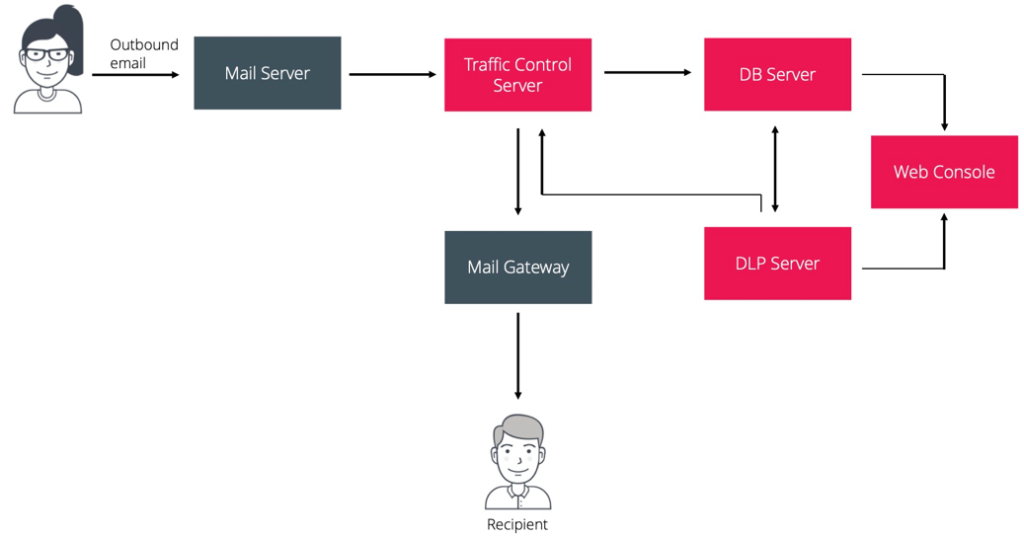
Benefits: A separate mail server, ease of settings on the mail server (most of the mail systems have this functionality), reliable email blocking.
With blocking: Web
Forwarding web traffic via ICAP to Zecurion Traffic Control server
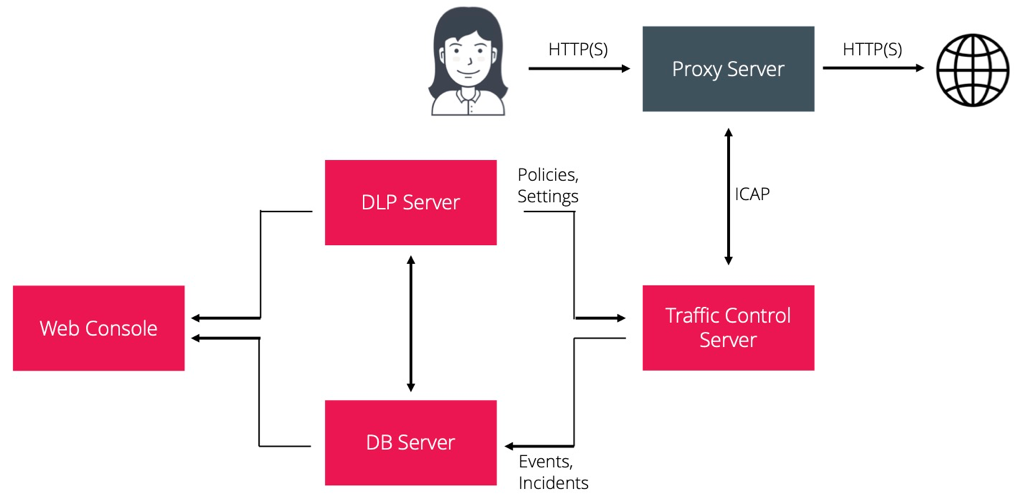
Benefits: Automated decryption of web traffic.
Note: The ICAP server-agent operation is supported in compliance with RFC 3507.
Installing Zecurion Secure Web Gateway with ICAP on the Traffic Control server
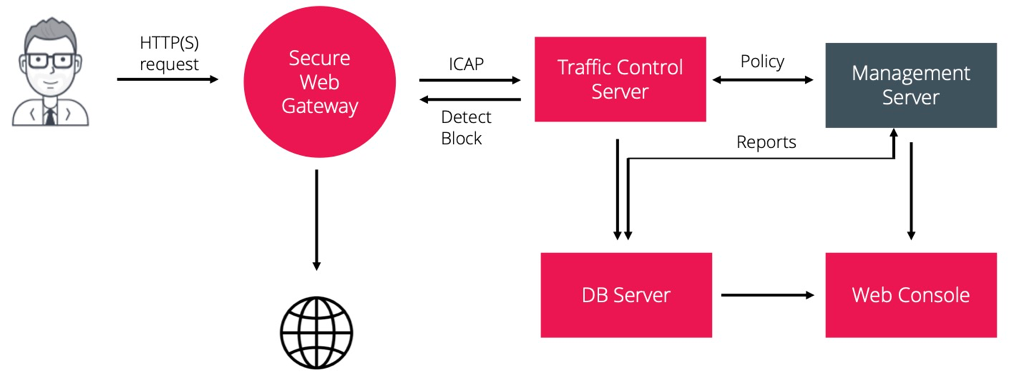
Benefits: A proxy server with categorization, content analysis and access policies.
Note: This type of deployment is using an internal certificate, cascade of proxy servers is not supported.
Using the Endpoint Traffic Control Agent
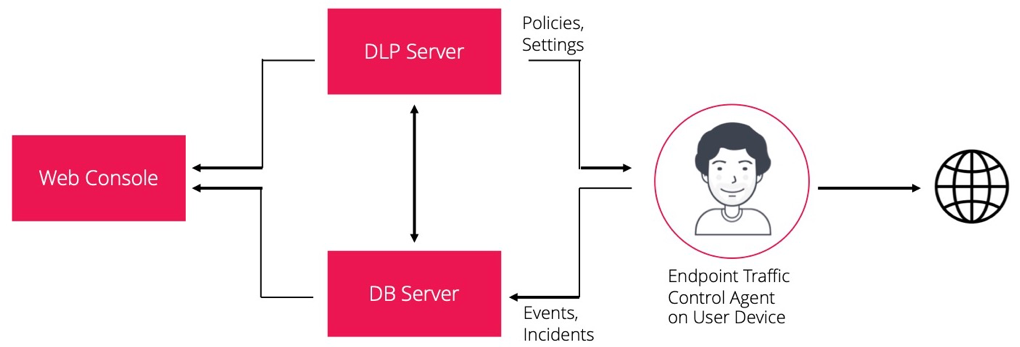
Benefits: Agent is installed on user PCs.
Note: The load on the user’s PC increases.
Without blocking: Email
Setting up a service mailbox on a mail server to copy emails from the required users
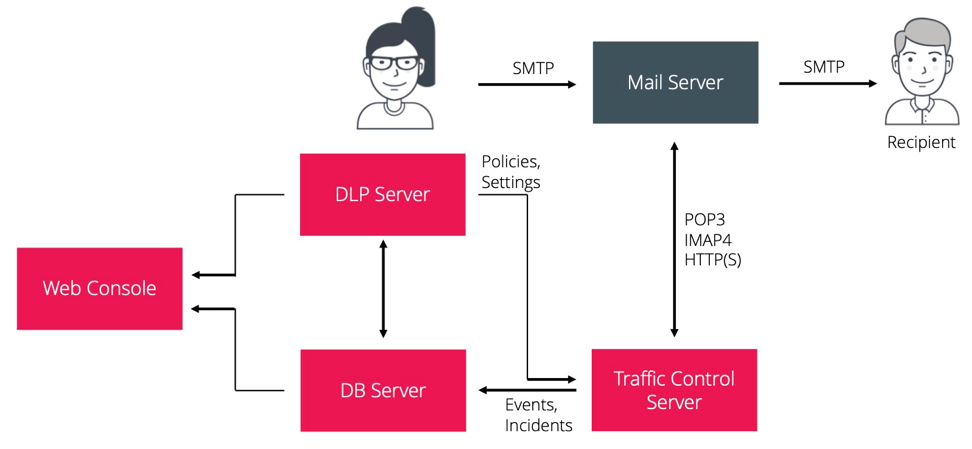
Benefits: Does not affect email traffic, you can maintain the server at any time.
Note: Installation on a separate server in the SMTP log analysis mode.
Using the Endpoint Traffic Control agent as a plug-in to an email client (MS Outlook, Thunderbird, IBM Lotus Notes)
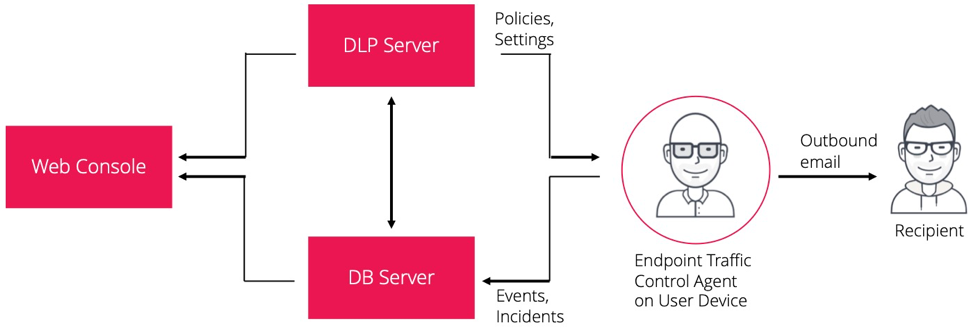
Benefits: Does not affect mail traffic, no need to use a server for traffic control.
Note: The load on the user’s PC hardware resources increases.
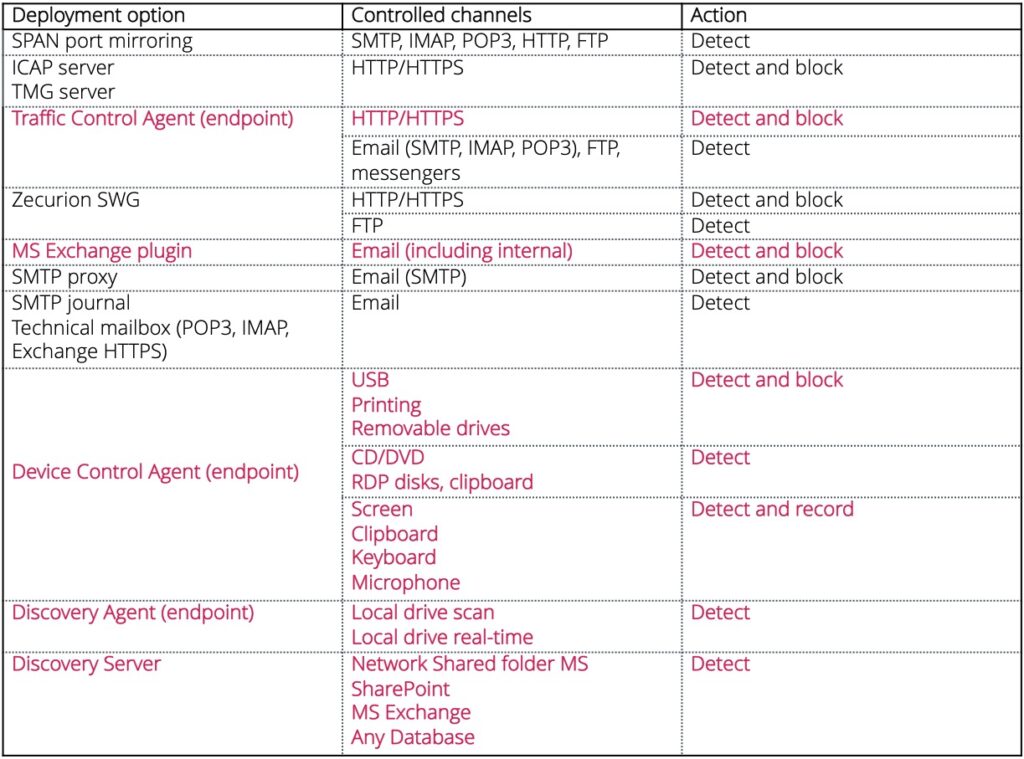
Learn about other deployment options from the table below. Options, particularly recommended by Zecurion technical experts, are highlighted.
Popular posts

One of the Largest Technical and Vocational Education and Training Service Providers in South Africa Uses Zecurion Next Generation DLP

One of the Largest World’s Upscale Hospitality Brands Protects Its Business in Turkey with Zecurion
Subscribe to our blog updates
You will receive only really useful emails and will always be able to unsubscribe from this mailing if, suddenly, your interests change
