DLP 12: KNOW MORE. RISK LESS.
People-centric approach: 360° protection from insider threats.
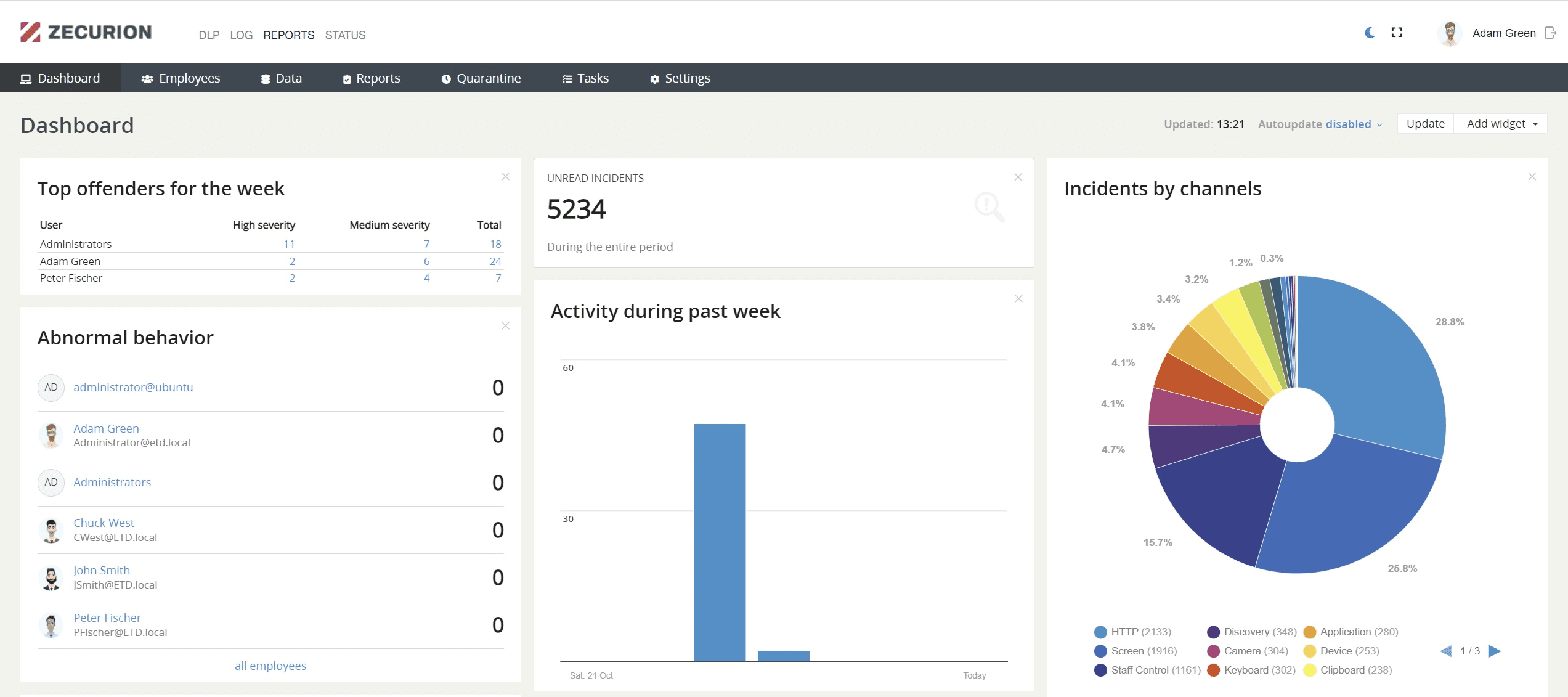
WHAT’S NEW?
01.
Dark theme
More interface options for a better user experience.
02.
Improved intuitive menu
Main sections list is now on top of the page, while navigation is on the left for ease of use.
03.
Enhanced policies
Quick search, editing, channels visibility, including optional DCAP Active Directory.
04.
Expanded access granularity
Access control per organizational unit (OU) enriches reports with total visibility of organization structure.
05.
Messengers under control
The system blocks messages, containing sensitive data in Telegram and Whatsapp.

ZECURION NEXT GENERATION DLP 12

MORE THAN A DATA LOSS PREVENTION
SCREEN PHOTO DETECTOR
This unique AI-based feature changes the game, stopping the insiders that were previously not being able to catch. Whenever someone tries to photograph a screen by the smartphone, Zecurion DLP immediately detects it via webcam and blocks the computer. The revolutionary technology uses 2 neural networks to ensure reliable smartphone detection and flags cybersecurity incidents in a blink of an eye (from 0.06 seconds).
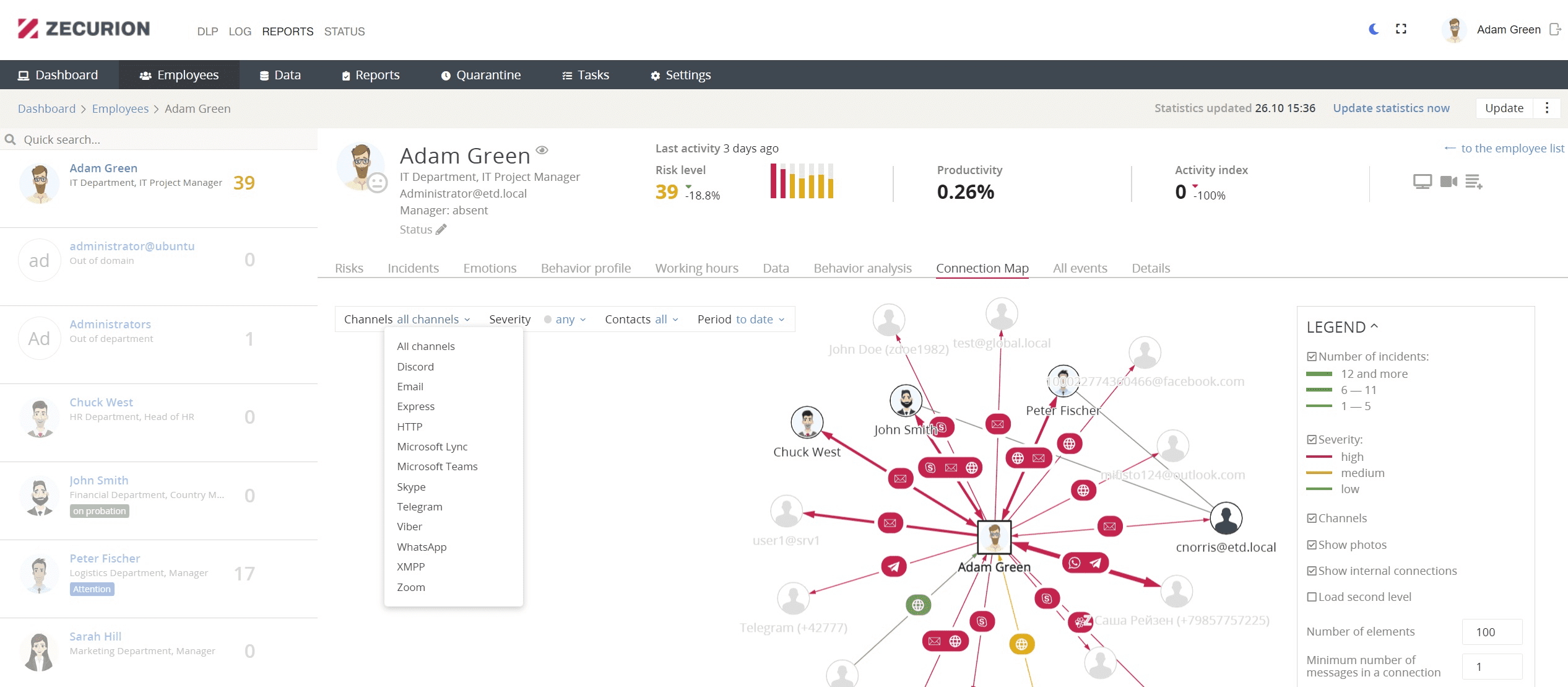
STAFF CONTROL
Staff Control keeps track of working hours, logs employees' actions at workplaces, and evaluates the efficiency. The module checks the activities of personnel for compliance with corporate standards and safety policies.
- Employee card. Each dossier contains detailed information on efficiency and activity at the workplace in dynamics. The Administrator can also review staff incidents in a convenient format.
- Report designer with 15 indicators. Now reports include a table with fast filters, groups, and data from up to tens of thousands of PCs.
- Resource usage and timesheets. Suggests detailed information on websites, applications running, and activity period.
INVESTIGATION WORKFLOW AUTOMATION
This module simplifies investigations and shortens the incident response cycle. It minimizes the cybersecurity team workload by providing a 360° view of actual tasks with all the statuses, data on the investigation stage, executants, and deadlines. During the investigation, cybersecurity team members can leave comments on the task and discuss progress with other participants (from CISO to analyst), attach documents and incidents as proof.
WHAT’S NEXT?
Contact us to consult with our experts, see demo or request extended presentation.