Communication Channels Mapping and Protection with Zecurion Traffic Control Module

Now that you know where your data, including confidential information, is stored, and decided, where and how do you plan to accumulate it, there are other important questions: How does this information move? Who sends it? Does the sender consider cybersecurity rules? Where does it go? Within the network, to the cloud, else?
Zecurion Traffic Control will easily answer these questions and will protect your sensitive data. Here are several tips for you on how and what to use the module for.
1. Intercept and analyze network communication across most protocols. Zecurion Traffic Control ensures total control of outgoing data over internet-connected channels, including email (SMTP, IMAP, POP3, MAPI), web-based email, social networks (Facebook, LinkedIn, Twitter, etc.), messaging platforms (WhatsApp, Telegram, Skype, etc.), and more.
You can analyze encrypted traffic too. Zecurion Traffic Control decrypts SSL connections using a man-in-the-middle (MitM) approach, providing full control of outgoing data even when using HTTPS. Thus, nothing will escape the network undetected.
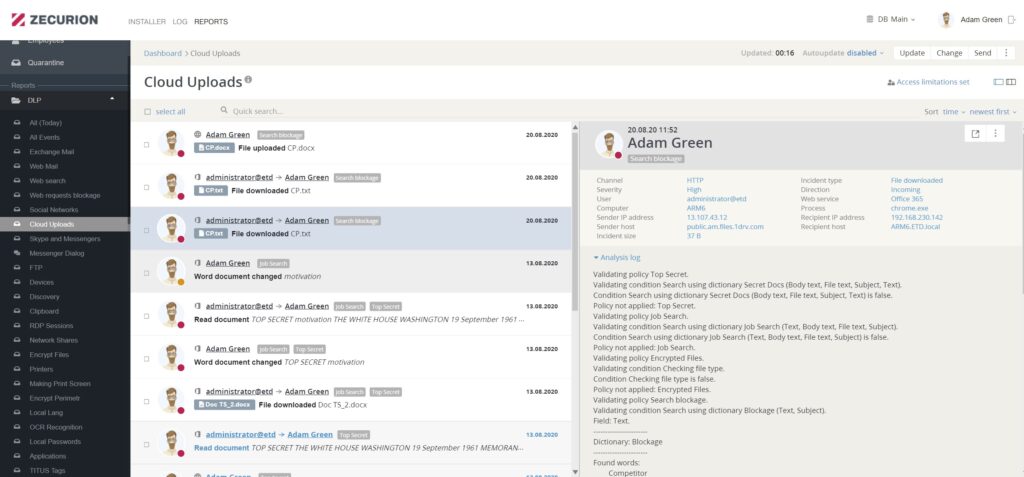
2. Pay attention to User Connection Map – it brings light to hidden communications and allows you to have a clear vision of data flow in and outside your corporate network. For advanced control, tracking and analysis of internal email traffic, use the special Microsoft Exchange plugin.
To foster safe communication at work, configure Zecurion Traffic Control to isolate suspicious emails for manual inspection for even better accuracy at identifying dangerous messages. Modify messages and remove sensitive information, leaving other files intact, after sending.
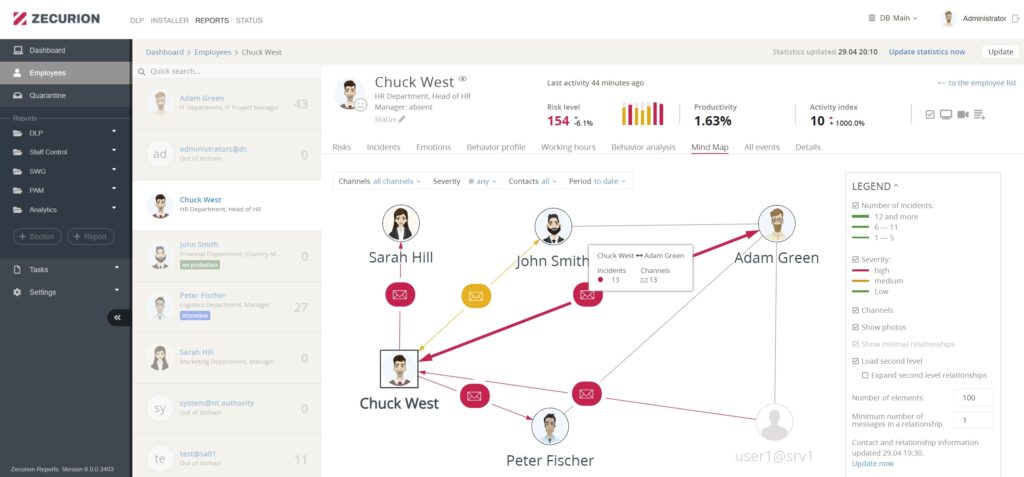
3. Respond to an incident faster. Traffic Control can notify the end user and IT security when an incident occurs. With the help of convenient dashboard, your cybersecurity team will view all actual tasks with all the statuses, data on the investigation stage, executors, and deadlines.
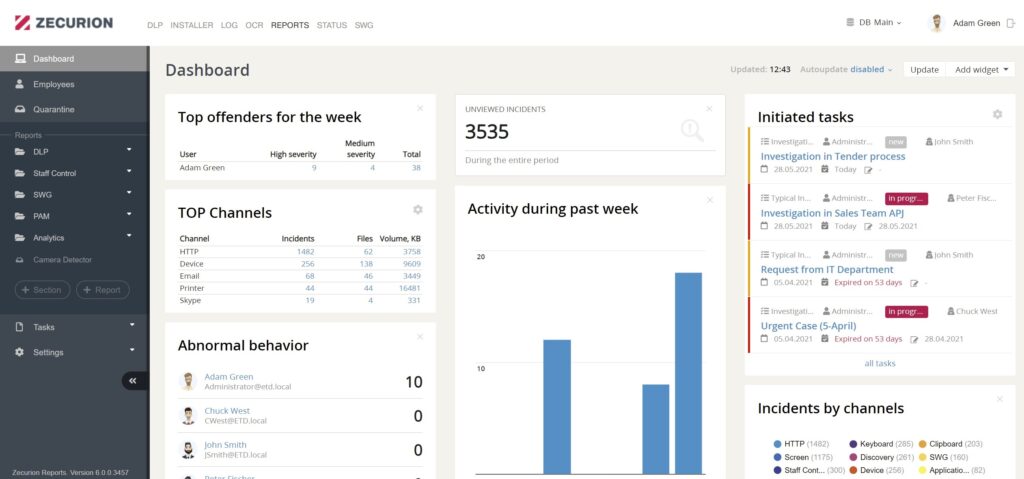
Last but not least, one of the primary strengths of Zecurion Traffic Control is the diversity of deployment options. Choose the most suitable one for your organization!
Zecurion Traffic Control can function as either an active filter (real-time options: endpoint agents, SMTP relay, Microsoft Exchange plugin, and more), passive mode options like SPAN port mirroring, or can be used in phased option – starting with a mirrored setup to allow for policies to be tested and tuned for maximum efficiency and then transitioning over to active filtering.
No matter what size your organization is or what your IT infrastructure looks like, Zecurion Traffic Control offers a fast and simple deployment capability.
Popular posts

One of the Largest Technical and Vocational Education and Training Service Providers in South Africa Uses Zecurion Next Generation DLP

One of the Largest World’s Upscale Hospitality Brands Protects Its Business in Turkey with Zecurion
Subscribe to our blog updates
You will receive only really useful emails and will always be able to unsubscribe from this mailing if, suddenly, your interests change
