Next Generation DLP for Forensic Investigations

How does Next Generation DLP help conduct forensic investigations?
The required tasks of the DLP, in general, include data analysis to perform incident management, control of data transfer over all channels, blocking data leaks, and information archiving. The difference is that standard DLP covers only compliance issues and detects data losses. Whereas the Next Generation incident management will allow you to find vulnerabilities, change policies, disclose fraudulent schemes, understand whether an employee is misusing his position/access rights, monitor the high-risk group, and finally review processes within the company.
How to manage incidents?
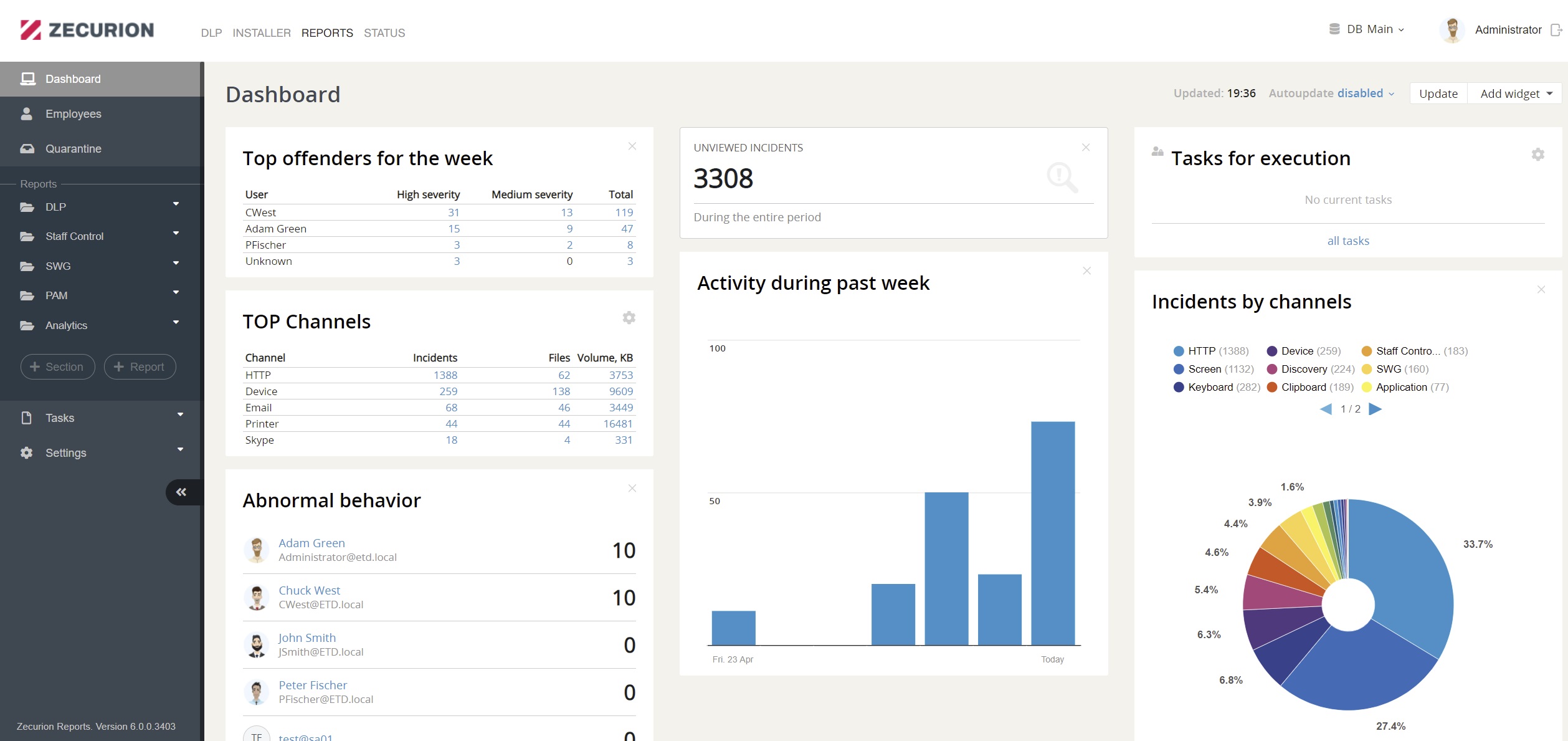
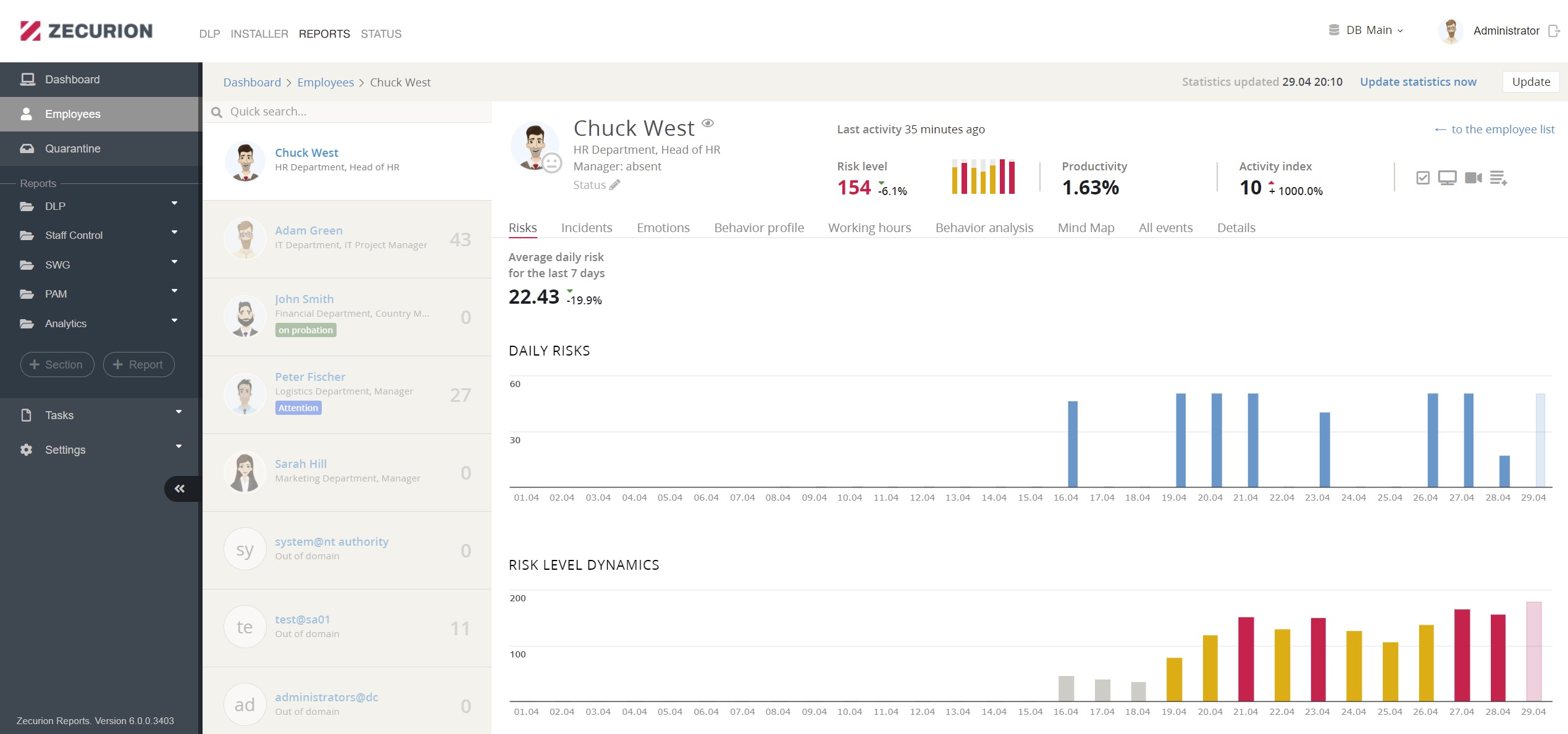
The Dashboard provides all crucial details in one place: control incidents and abnormal behavior promptly.
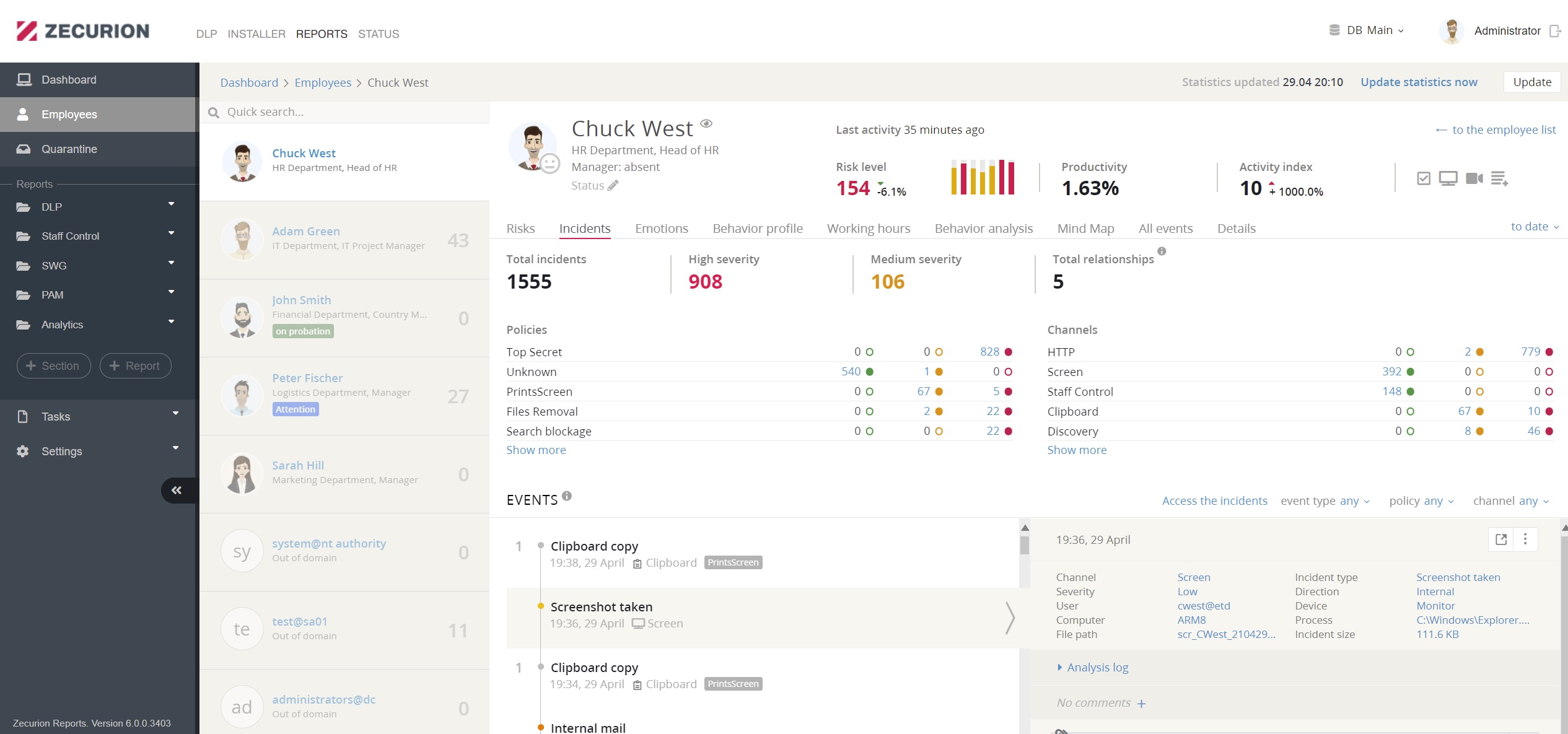
User incident profile allows you to see all events associated with an employee. Here you see their violations, with whom an employee communicates, what data they use in work.
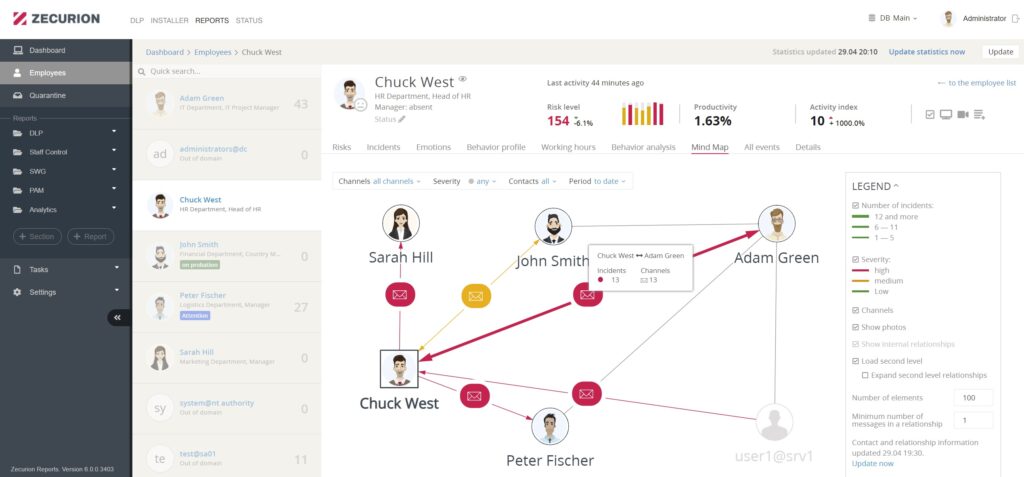
The connections diagram will highlight suspicious communication and contacts between employees (hidden connections within an organization).
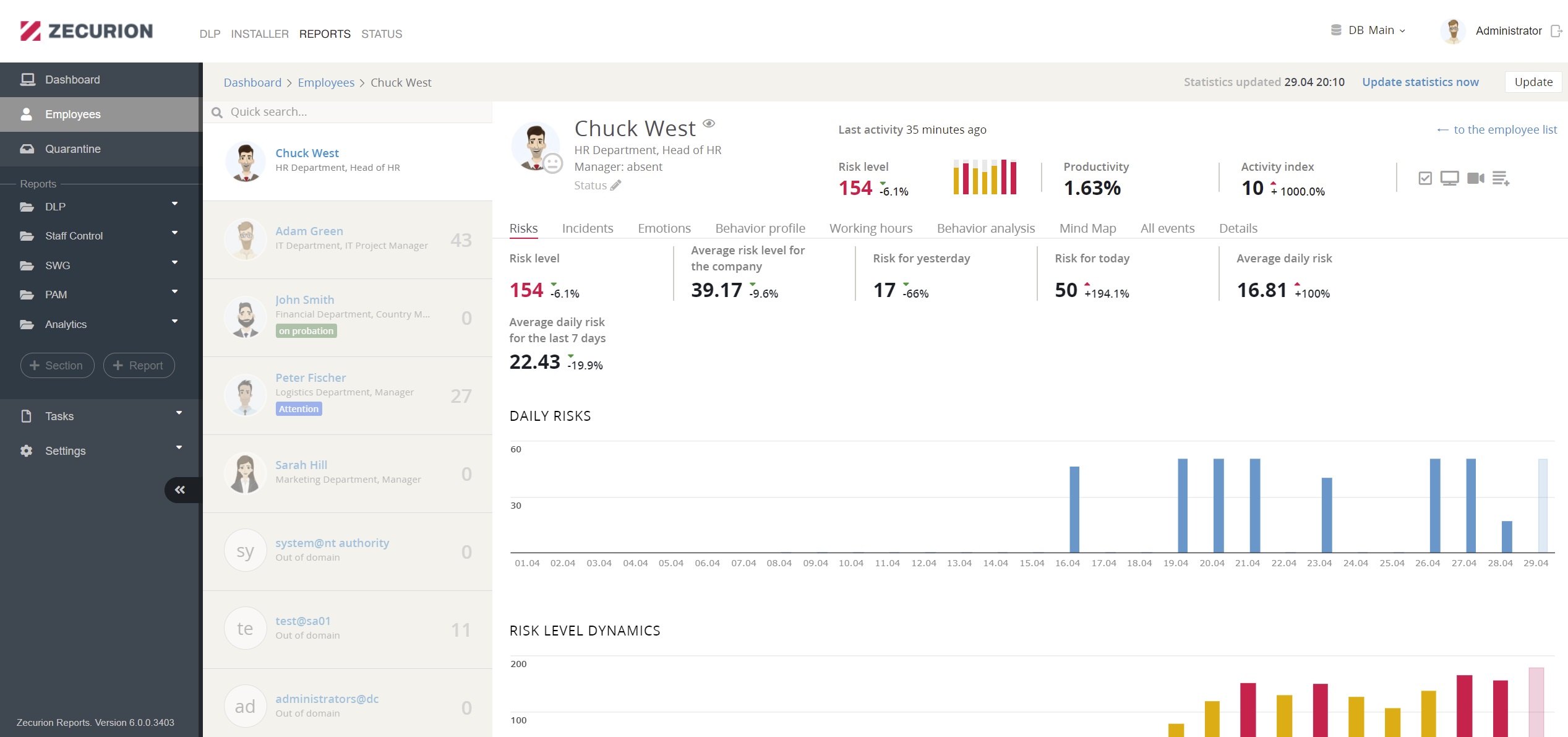
Risk-based assessment reports, together with the ability to quickly search in a data archive, will assure that all departments (Management, HR, Security Team) will be informed about any changes before data leak or any illegal action happens.
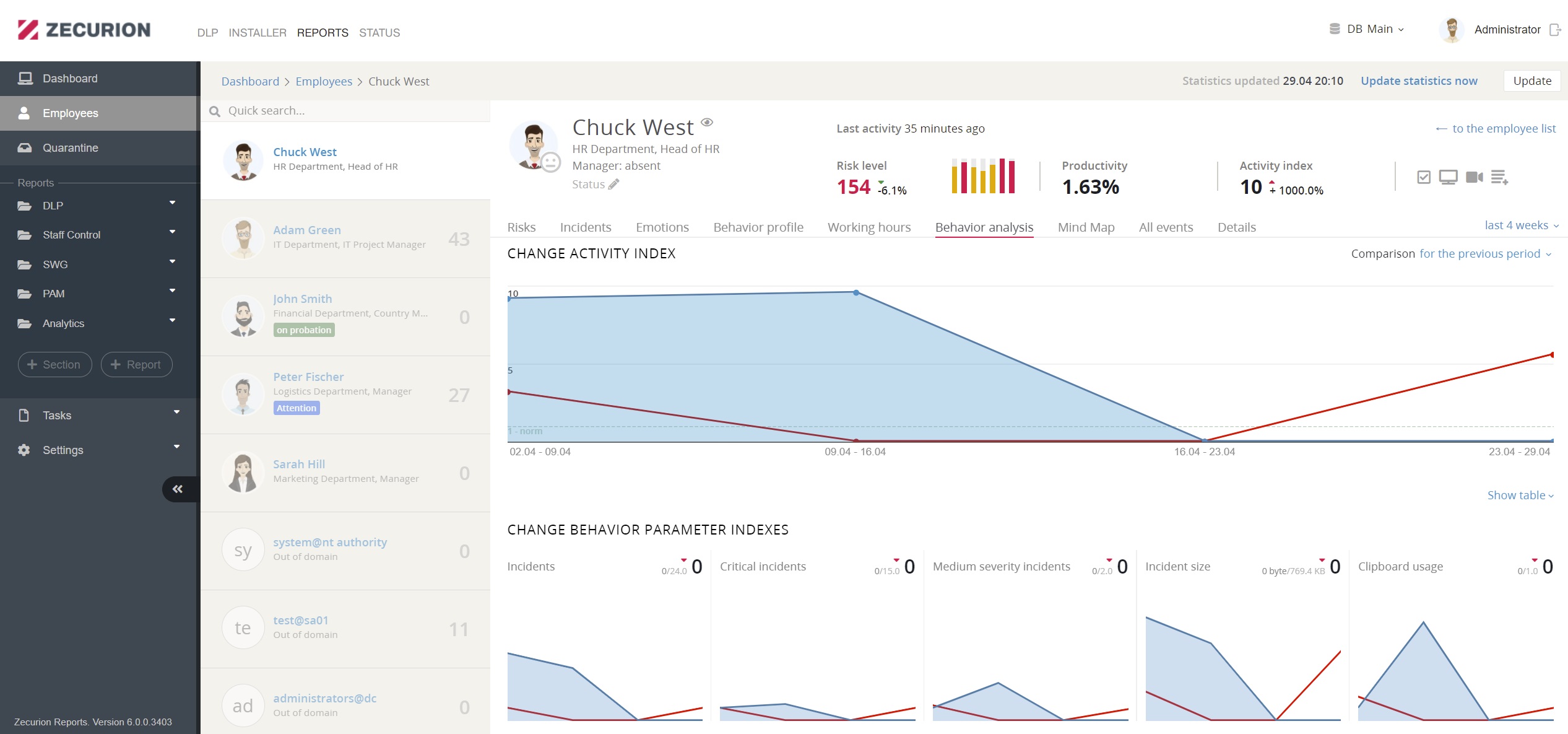
Behavioral analysis and UBA ensure total visibility of employee activity and evaluate it on main parameters: risk, productivity, policies, and emotional state. Each employee profile contains all events associated with the user on a single page. All events are shown in chronological order and are clickable for more information. The Security Officer will supervise high-risk employees, while low-risk ones will operate with more minor limitations.
How to investigate a cybercrime
Step 1: Assess the initial input. Answering standard “who, what, where, when, why” and “how” questions will be enough at this stage:
- Who are the violators?
- What violations are committed?
- When were they executed?
- What type of evidence is available? Is evidence saved and maintained correctly?
- Why do violations happen? Were there any behavioral “red flags” before the incident?
- How was the insider scheme organized? Can we track the communication chain?
With Zecurion’s powerful easy-to-generate reports, you can analyze and quickly drill down to a specific incident in a few clicks to receive all answers.
Step 2: Collect possible evidence. According to the International Association of Chiefs of Police, the typical electronic devices providing digital evidence are the following:
- Web camera – pictures, screenshots, videos;
- Cell phone – text and audio messages, call logs, applications used, social media accounts, everything from all categories;
- Computer/laptop – everything from all categories, social media accounts, Internet search history, documents, emails;
- Tablet – everything from all categories, applications used, social media accounts;
- File storage (hard drive, thumb drive, optical media, etc.) – everything from all categories.
Mainly to collect devices, investigate, what’s in there, and conduct an initial assessment, investigators will need a warrant. In case when one device is suspected to be a part of several crimes, multiple documents will be required. The bureaucratic process takes time.
In the case of Zecurion Next Generation DLP, you already have access to all corporate devices, communication channels, and archives, and you don’t need any warrants for investigation, as you initially have all required consents from corporate users.
Zecurion Next Generation DLP has user session recording, keyboard recording, webcam and microphone recording, Screen Photo Detection, and many other unique features to obtain any possible evidence.
With Zecurion’s archive of files and messages, you will not bother whether the possible evidence is secure. All intercepted data – files, messages, incidents, events, and more – are stored in a database, so you have everything you need to generate detailed reports, conduct a comprehensive forensic investigation, and gather evidence for legal actions.
Step 3: Analyze results with a legal team. By 2021 Zecurion has helped numerous companies identify appropriate charges and provide proper factual support to forensic investigation.
One more bonus from Zecurion is Investigation Module. This module simplifies collaboration within security teams during investigations and shortens the incident response cycle. It minimizes the cybersecurity team workload by providing a 360° view of actual tasks with all the statuses, data on the investigation stage, executants, and deadlines. During the investigation, cybersecurity team members can leave comments on the task, discuss progress with other participants (from CISO to analyst), and attach documents and incidents as proof.
Popular posts

One of the Largest Technical and Vocational Education and Training Service Providers in South Africa Uses Zecurion Next Generation DLP
Subscribe to our blog updates
You will receive only really useful emails and will always be able to unsubscribe from this mailing if, suddenly, your interests change