Screen Watermarks and Screen Photo Detector: How to Discover Insider Threats Before They Become an Incident

An employee can overplay software. There are quite a few limitations for software – legal, technical, - and there are no limits to human savvy. Whatever vendors do, people are still smarter than machines.
If an employee tries to send some sensitive data over communications channels, or even share it outside the corporate network, he will receive a long conversation with Security Officer, who will be notified straight away (with the Next Generation DLP) or after a threat became an incident (usually with the ordinary DLP). Knowing this, an employee might go two ways instead.
- Make a screenshot and send it peacefully.
- Take a picture on a personal phone to take information he needs with no risks.
Both actions will be managed by Zecurion Next Generation DLP. Let’s see how.
Zecurion Screen Watermarks
The Security Officer can set watermarks with the name of a user, PC, and date over certain windows (e.g., MS Office, CRM, and other). The screenshot will initially show all information, when and by whom exactly it was created. This feature will make users reconsider their further actions.
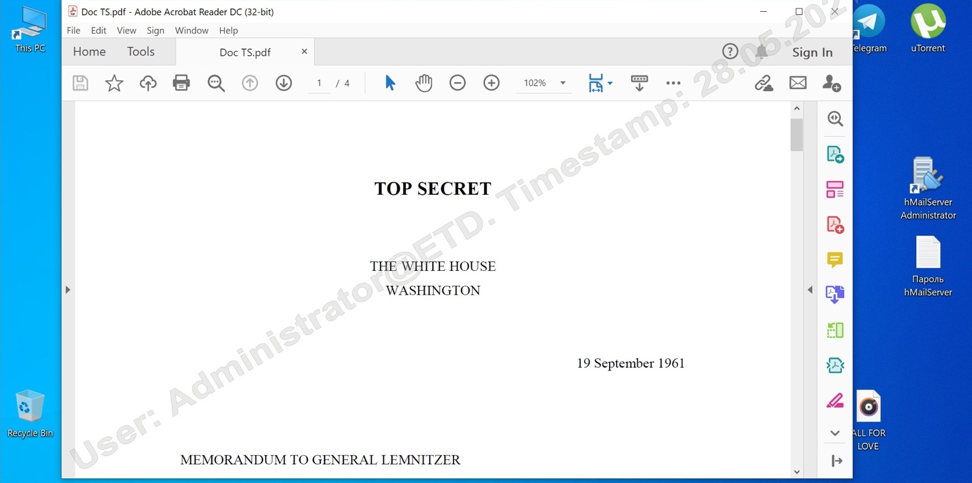
If circumstances require more rigid measures, the Security Officer can block the option of screenshots on the user’s PC.
Screen Photo Detector
Whenever someone tries to photograph a screen by a smartphone, this AI-based Zecurion DLP feature immediately detects it via webcam and blocks the computer.

The revolutionary technology uses 2 neural networks to ensure reliable smartphone detection and flags cybersecurity incidents in a blink of an eye (from 0.06 seconds).
Screen Photo Detector works with any smartphones, confidently recognizes objects in poor lighting or with visual noises, and is optimized to work with tens of thousands of workstations. After identifying the incident, the Module allows darkening (shut down) the user’s screen or temporary block him.
Both technologies are integrated with Zecurion Next Generation DLP: are managed through a single console from the Administrator’s PC, mobile devices or application for iPad.
Popular posts

One of the Largest Technical and Vocational Education and Training Service Providers in South Africa Uses Zecurion Next Generation DLP

One of the Largest World’s Upscale Hospitality Brands Protects Its Business in Turkey with Zecurion
Subscribe to our blog updates
You will receive only really useful emails and will always be able to unsubscribe from this mailing if, suddenly, your interests change
